30+ data flow diagram threat model
The resulting document is the threat model for the application. Threat Dragon TD is used to create threat model diagrams and to record possible threats.

Threat Modeling Demystified
The original intent of a data flow.

. In this step Data Flow Diagram should be divided in the context of Model View Controller MVC. A data-flow diagram shows how a certain type of data flows from one part of a system to another. Once added they can be.
Add model elements to your diagram by clicking or tapping the relevant shape in the stencil on the left side of the diagram editor. Ad Develop a Step-by-Step Visual Guide to Different Processes. Approach your data-flow diagram with the right threat model focus.
Threat modeling uses traditional Data Flow Diagrams DFDs 8 with security-speciflc annotations to describe how data enters leaves and traverses the system. Are Data Flow Diagrams Enough. Learn More About Different Chart and Graph Types With Tableaus Free Whitepaper.
To create a data-flow diagram you can use an online collaborative drawing tool like Google. A threat model diagram is a visual form of threat model. Threat Modeling Security Fundamentals.
Process Flow Diagrams PFDs vs. Use Lucidchart to visualize ideas make charts diagrams more. Automated threat modeling software using process flow diagrams allow defenders to approach their systems from the same vantage point as attackers architecturally.
Data-flow diagram elements 3 min. Threat modeling analyzes how an adversary might attack a system by supplying it with malicious data or interacting with it. Ad Explore Different Types of Data Visualizations and Learn Tips Tricks to Maximize Impact.
Use Lucidchart to visualize ideas make charts diagrams more. Choosing a Practical Threat Model Diagram Approach. Ad Download free chart software to easily create data flow diagrams.
Save Time by Using Our Premade Template Instead of Creating Your Own from Scratch. Data Flow Diagrams DFDs in the Threat Modeling Arena While DFDs are used to document the flow of data in out and around a system application or. Use data flow diagrams for a profound understanding of your application Now that you know more about the why and how of threat modeling it is time to take a deeper look into the data.
Data flow diagrams therefore are generated as a means of communicating this to the outside world those who are not threat modelers. One large project at. Process - The task element 7 min.
The analysis uses a Data Flow Diagram DFD to describe how data. Ad Lucidcharts data flow diagram software is quick easy to use. This module is part of these learning paths.
Data store - The. Microsofts Threat Modelling Tool This tool identifies threats based on STRIDE threat model classification and is based on Data Flow Diagram DFD which can be used to. DFD-based threat models do not integrate well in a production environment built around an Agile methodology.
Threat Model Thursday. Visual Paradigm Online features an online threat model maker and a large variety of technical and. Create threat models online.
Threat modeling is an effective technique to help you identify threats and ways to reduce or eliminate risk. User Login Data Flow Diagram for the College Library Website. Processes data stores and actors.
This weeks threat model Thursday looks at an academic paper Security Threat Modeling. Ad Lucidcharts data flow diagram software is quick easy to use.
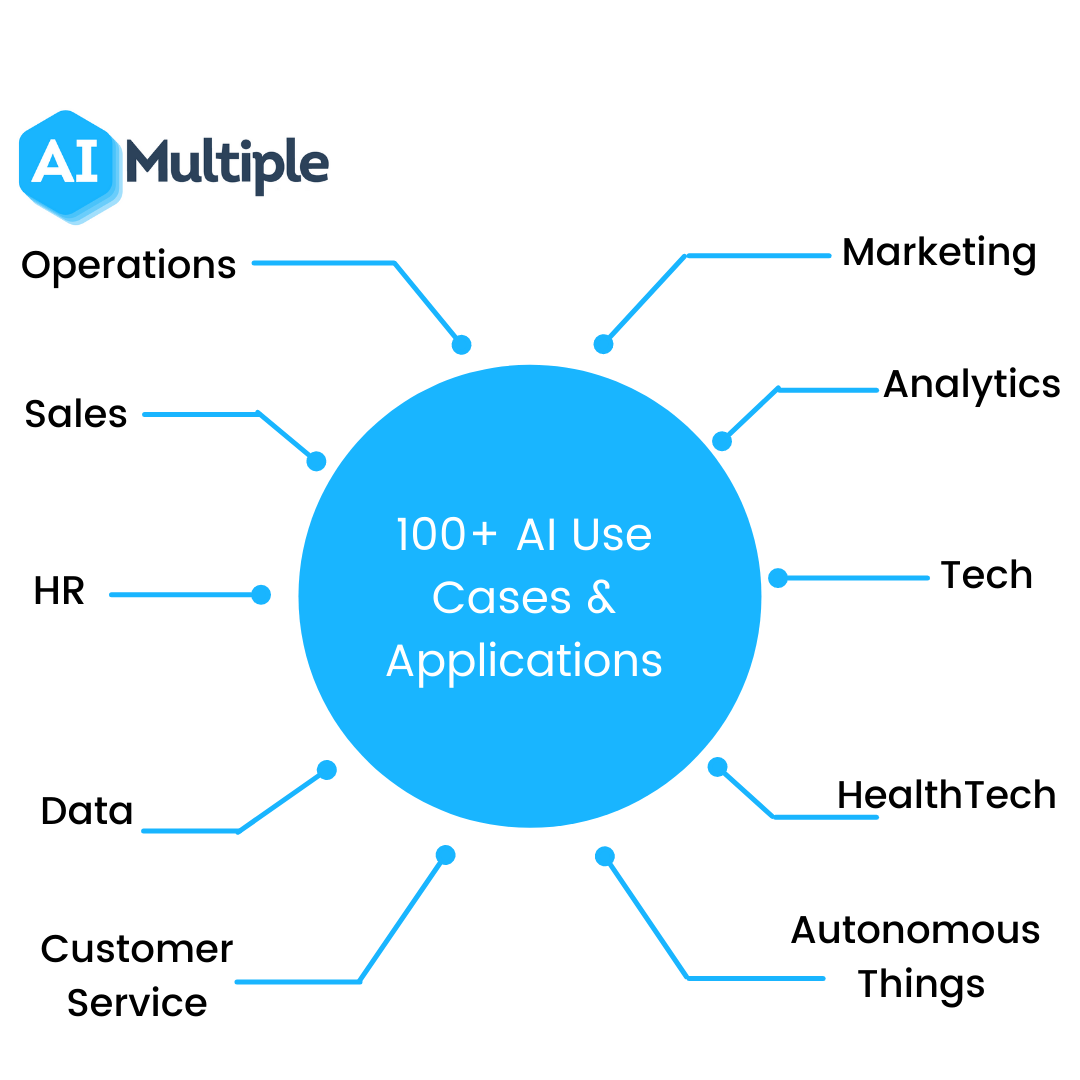
100 Ai Use Cases Applications In 2022 In Depth Guide
![]()
Threatmodeler About The Evolution Of Threat Modeling
Bill Of Materials For Responsible Ai Collaborative Labeling Snorkel Ai
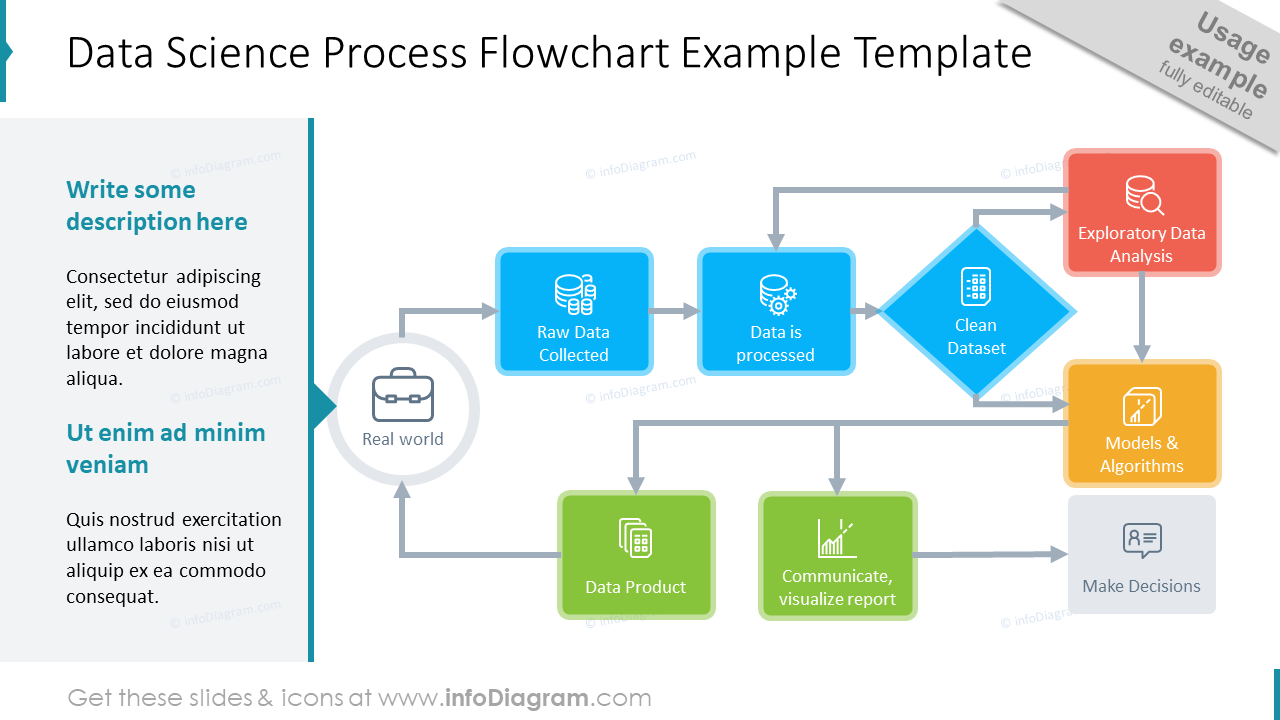
30 Data Science Line Icons Of Big Data Predictive Analytics Definitions Processes As Powerpoint Presentation Infographics
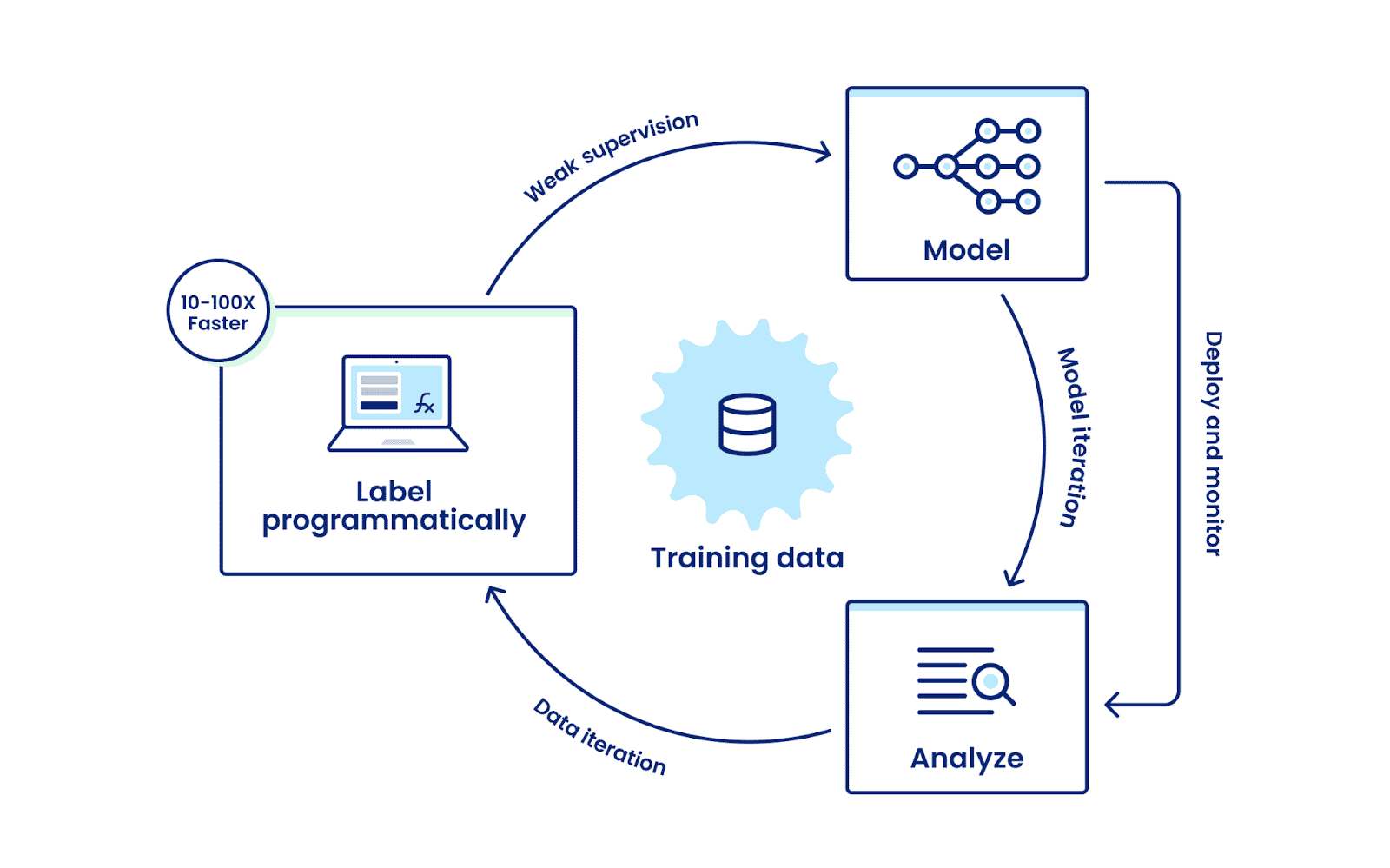
Introducing Continuous Model Feedback To Drive Rapid Data Quality Improvement Snorkel Ai

What Is Data Pipeline Types Components And Use Cases
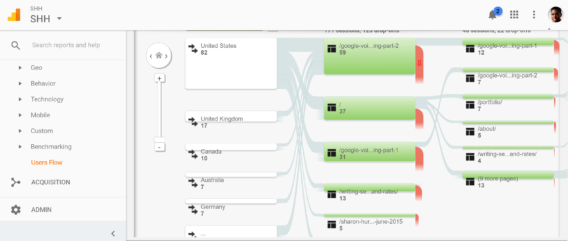
How To Design A User Flow Diagram For Your Website

Threat Modeling Demystified
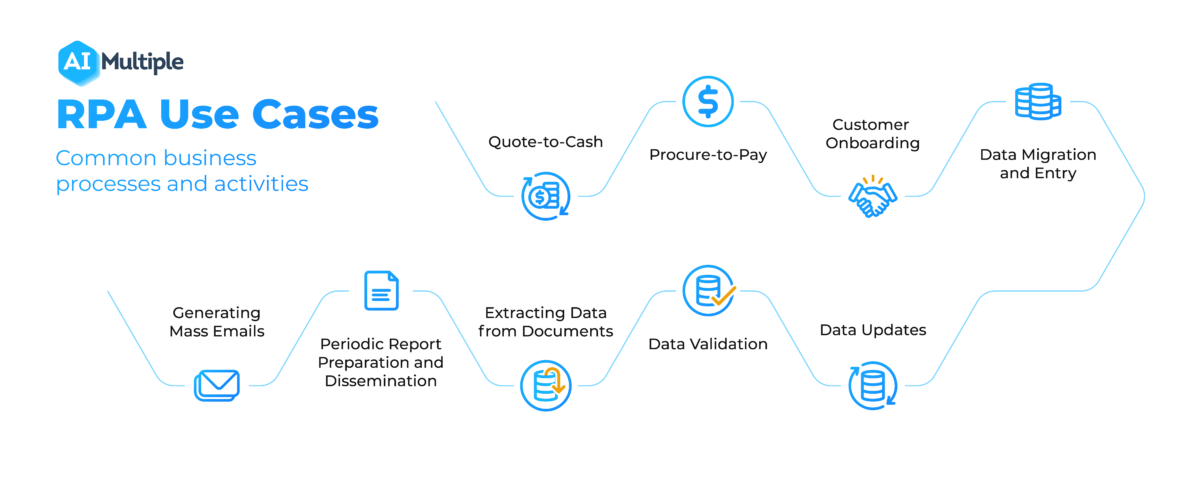
T2isd79la4he3m

A Threshold Based Real Time Analysis In Early Detection Of Endpoint Anomalies Using Siem Expertise Sciencedirect

Threat Modeling Demystified

Bill Of Materials Bom As A Foundation For Plm Erp Mes Integration Prostep Us
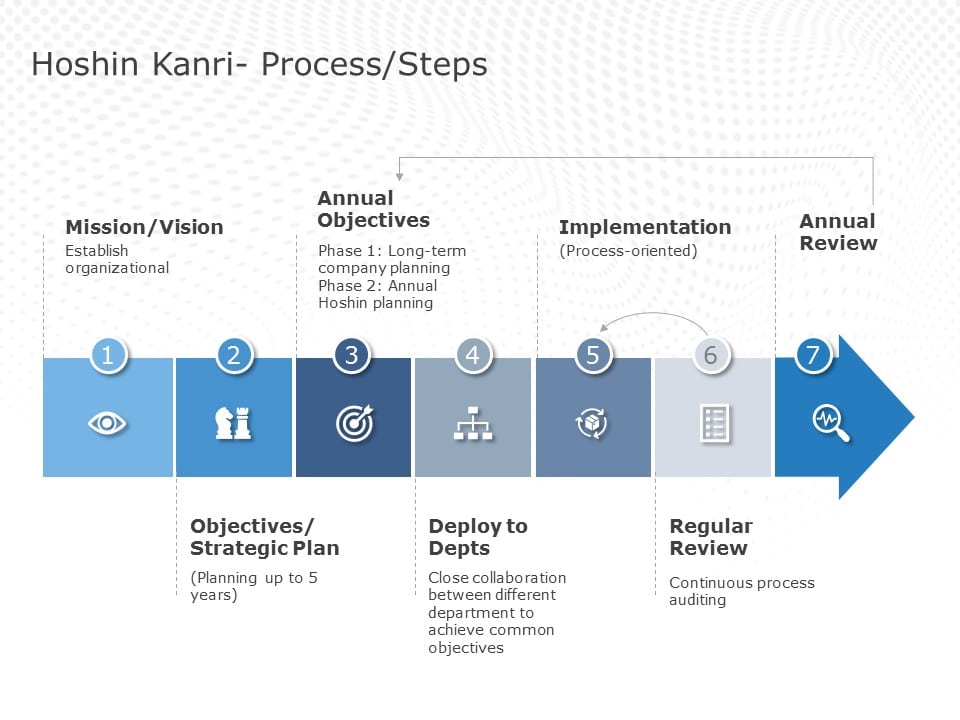
1567 Editable Free Flow Chart Templates Slides For Powerpoint Presentations Slideuplift
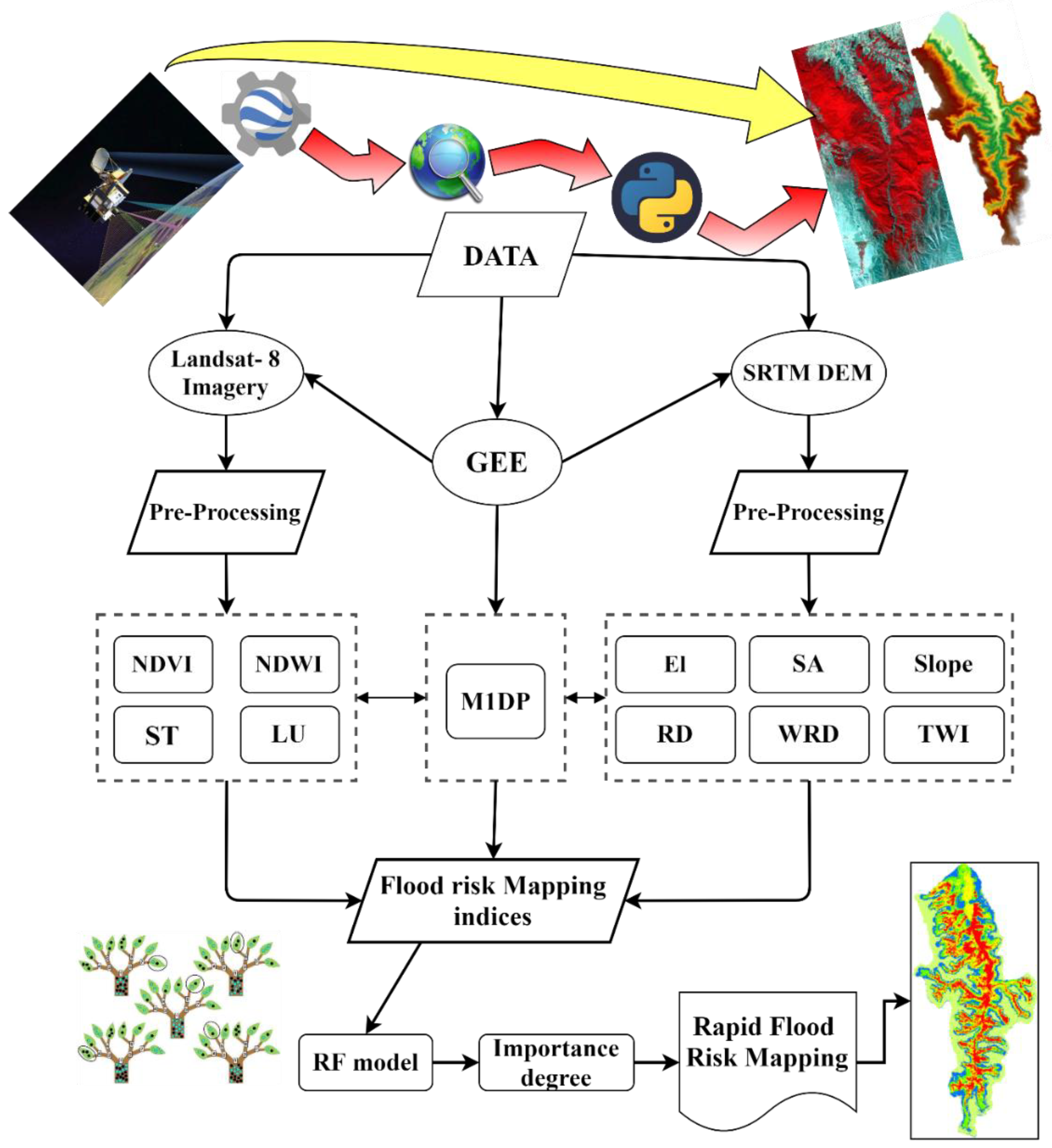
Water Free Full Text Flood Risk Mapping By Remote Sensing Data And Random Forest Technique Html
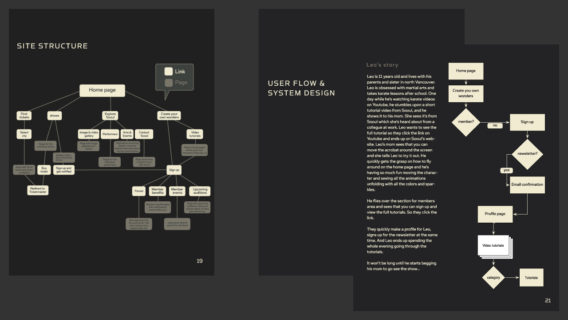
How To Design A User Flow Diagram For Your Website

Real Time Operational Monitoring Of Renewable Energy Assets With Aws Iot Aws For Industries

Threat Modeling Demystified